Introduction to cryptos
1. Introduction
A cryptocurrency (or crypto) is a digital currency that does not rely on any central authority to uphold or maintain it. The technology underlying cryptocurrencies is the blockchain. Essentially, a blockchain is a database shared over a network of computers called nodes. It is structured as a growing sequence of data blocks chained together cryptographically. Crypto transaction data are “packed” into blocks that are sequentially appended to the blockchain dataset. Each block is chained to the previous one using cryptography, and this guarantees the integrity of the data. Every blockchain protocol sets its own rules governing how “consensus” should be reached. By “consensus” we mean a general agreement on the state of the blockchain (Garavaglia, 2022). The most important types of consensus mechanism are proof-of-work and proof-of-stake. In proof-of-work blockchains, such as Bitcoin, you can append a block to the blockchain only if you have sorted out the right solution to a complex mathematical problem. In this way, you demonstrate that you have spent some computational work to build and append the block (“mining”). In proof-of-stake blockchains, such as Ethereum, you must hold a “stake” of the associated (“native”) cryptocurrency to append blocks to the blockchain.
In 2008, the first cryptocurrency, Bitcoin, was created. Bitcoin was introduced in the white paper Bitcoin: A Peer-to-Peer Electronic Cash System (Nakamoto, 2008). The true identity of Satoshi Nakamoto is still today a mistery. In the following years, Bitcoin pioneered the boom of cryptocurrencies. According to CoinMarketCap, accessed on 2022-09-12, nowadays exist more than 20.9 thousand cryptos. The market cap of the entire crypto market is $1.02 trillion, less than the capitalization of a single company such as Apple ($2.54 trillion as of 2022-09-13) or Microsoft ($1.92 trillion as of 2022-09-13). To give an idea of the relevance of cryptocurrencies as opposed to other asset classes, as of 2021 the world bond market outstanding was $124.4 trillion, and the world stock market had a market capitalization of $126.9 trillion (Securities Industry and Financial Markets Association, 2022).
The first cryptocurrency by market cap is Bitcoin ($433.78 billion as of 2022-09-13), followed by Ethereum ($212.97 billion as of 2022-09-13). The combined Bitcoin and Ethereum capitalization roughly represents 60% of the overall crypto market.
Table 1 lists the 10 largest cryptocurrencies by market capitalization according to CryptoCompare, data downloaded on 2022-09-13. For each crypto, we report the symbol, the market capitalization in US dollars, the type of consensus mechanism, and the launch date.
| Crypto | Symbol | Market cap. (bn) | Consensus mechanism | Launch date |
|---|---|---|---|---|
| Bitcoin | BTC | $433.78 | PoW | 2009-01-03 |
| Ether | ETH | $212.97 | PoS | 2015-07-30 |
| Tether | USDT | $67.79 | n.a. | 2014-10-06 |
| USD Coin | USDC | $51.49 | n.a. | 2018-10-31 |
| Binance Coin | BNB | $48.54 | PoSA | 2017-06-27 |
| Ripple | XRP | $35.64 | XRP LCP | 2013-01-01 |
| Solana | SOL | $20.37 | PoH | 2017-11-01 |
| Binance USD | BUSD | $20.16 | n.a. | 2019-09-10 |
| Cardano | ADA | $17.03 | PoS | 2017-10-05 |
| Polkadot | DOT | $9.75 | NPoS | 2020-08-18 |
PoW: Proof-of-Work
PoS: Proof-of-Stake
PoSA: Proof-of-Staked-Authority
NPoS: Nominated Proof-of-Stake
XRP LCP: XRP Ledger Consensus Protocol
PoH: Proof of History
2 Exploring Bitcoin
2.1 The Bitcoin network
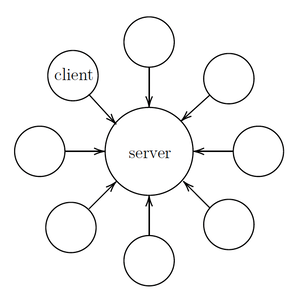
As we have anticipated in the Introduction, the blockchain database is shared over a network of computers. In this subsection, we will explain in details how the Bitcoin network works. However, before doing so, we must clarify some basic concepts. Bitcoin, email, and the World Wide Web are all Internet technologies based on a network of interconnected computers. These computers are called “nodes”. Within a network architecture, there are computers that provide some services (servers), and computers that request these services (clients)[1].
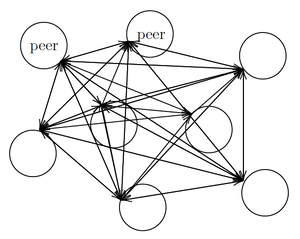
There is no single network architecture. In a centralized client-server model, there is a centralized (group of) server(s) providing services to clients. See Figure 1. In a peer-to-peer (P2P) model each node acts both as a server and as a client with respect to its peers. In a peer-to-peer model the nodes are all “equal” and contribute to deliver network services. See Figure 2.
The Bitcoin blockchain is a peer-to-peer network maintained by thousands of full nodes, i.e. nodes that download and sync the entire blockchain ledger or part of it (pruned nodes), and independently verify block and transaction data before transmitting it to other nodes[2] Therefore, full nodes contribute to improve the security and decentralization of the network. Full nodes also serve lightweight nodes, i.e. nodes that store block headers only and rely on full nodes for retrieving everything else on demand (Bitcoin website, accessed on 2022-08-17). While full nodes drain a significant amount of computational power and disk space, lightweight nodes can also run on resource-constrained devices, such as smartphones.
Both full and lightweight nodes can include additional functionality, like a wallet. Wallets will be explained in Subsection 2.4. Furthermore, some nodes include the mining function, i.e. the capability of building blocks of transaction data and adding them to the blockchain database. These nodes are called “mining nodes” or “miners”. The mining activity will be explained in Subsection 2.2.
When a new transaction occurs, it is propagated from the originating node over the whole network. Before routing information to peers, each node performs a consistency check with the data already included in the blockchain. Nodes temporary store pending transactions in the so-called mempool, which is a sort of waiting room. Each node has its own mempool, and mempools are not perfectly synchronized across nodes.
2.2 Consensus mechanism
In the previous section we said that the Bitcoin system relies upon a network of computers (nodes) which are all peers. These nodes distrust each other. How can distrustful network participants reach consensus about the state of the blockchain dataset? This is made possible by the adoption of a consensus mechanism. A consensus mechanism is the set of rules that governs how to reach a general agreement about the state of a blockchain database. Every blockchain has its own consensus mechanism. The type of consensus mechanism adopted by Bitcoin is called “proof-of-work” [3].
In Bitcoin’s proof-of-work, miners are required to spend some computational power to participate in a competition. The competition is articulated as a sequence of rounds. Each round consists in looking for a solution to a complex mathematical problem associated with a block of pending transactions. The solution to the mathematical problem is needed for appending the block to the blockchain. Therefore, miners do two things:
- build a block of transaction for each round of the competition;
- try to solve a mathematical puzzle associated with the block.
In case a miner is successful in a round of the competition, it broadcasts the solution to the network. According to Decker and Wattenhofer, 2013 the median time for a peer to receive a block is 6.5 seconds, while the mean value is 12.6 seconds. After 40 seconds, 95% of the peers have received the block. Each peer verifies that the block’s transactions are legitimate, and the solution is correct. If this is the case, the block is appended to the blockchain, and the miner gets rewarded. All the other miners have lost a round of the competition. The following round immediately begins. Each miner starts building a new block and looking for a solution to the relative cryptographic puzzle.
By imposing some work to add a block to the blockchain, “proof-of-work” cryptos guarantee the security of the blockchain and prevent fraudulent behavior. First, miners are discouraged to cheat. If they do so, they will be spotted by their peers. Cheating miners will incur in a cost (the energy utilized to solve the mathematical problem) and won’t earn any revenue, as they won’t get the reward. Furthermore, to alter a transaction included in a block of the blockchain, you need to re-do the computational work associated with that block and with all the subsequent blocks in the blockchain sequence. Therefore, as new blocks are appended on the top of a certain block, altering the block’s transactions becomes more and more difficult. After some blocks, blockchain entries become almost immutable.
2.2.1 The blocks of pending transactions
Let’s explain how miners build blocks of pending transactions. To do that, they “pick” pending transactions from the mempool where they are stored, and “pack” them into blocks. They build a new block for each round of the competition. Block size is constrained to 4 million weight units, which are equivalent to a theoretical maximum capacity of 4 megabytes. The block space is not allocated according to a pre-defined rule, i.e. miners can discretionary choose which transactions to include in a block.
2.2.2. The mathematical puzzle
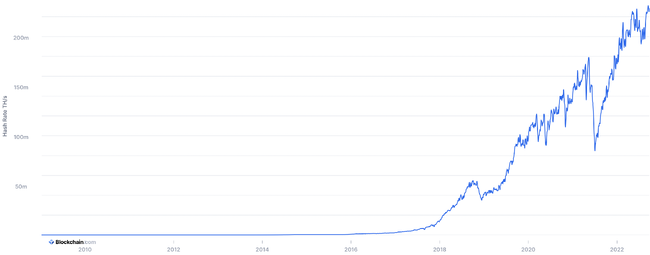
The difficulty of the mathematical problem is adjusted every 2016 blocks (approximately 2 weeks) in such a way that on average a new block is mined every 10 minutes. Therefore, the larger the computing power engaged in solving the puzzles, the higher will be their difficulty. The total computing power absorbed by the mining activity is measured by the hash rate, which is the number of calculations per second the network can make. For example, if the hash rate is 10 Th/s (terahashes per second), this means that the network can make 10 trillion calculations per second (Bitcoin website, accessed on 2022-08-17). Figure 3 reports the estimeted total hash rate of the Bitcoin network from its origins to September 25, 2022 (Blockchain.com, accessed on 2022-09-26).
2.2.3 The reward
When a miner successfully mines a block, it obtains a reward. Since the reward is attributed with a transaction included in the block (“coinbase transaction”), the miner does not get rewarded in case of block rejection by its peers. For example, if a block contains a double-spending transaction, network nodes won't accept it and the coinbase transaction won’t become part of the blockchain history. The reward comprises two components: a number of newly issued bitcoins and the fees associated with block transactions (Antonopoulos, 2017).
A number of newly issued bitcoins. This is the only way bitcoins are issued, i.e. every bitcoin is initially created as a mining reward. The number of newly-issued bitcoins per mined block, initially set to 50 in 2008, is halved every 210.000 blocks (approximately every 4 years). Currently, 6.25 new bitcoins are injected into circulation every time a new block is mined. The total Bitcoin supply is capped at 21m bitcoins, and it is expected to be reached in 2140. As of today, the circulating Bitcoin supply amounts to more than 19m bitcoins, i.e. more than 90% of the total Bitcoin supply has already been issued.
The fees associated with block transactions. Users pay fees to miners as an incentive to process their transactions. The fee amount is not predefined, and can be arbitrarly chosen by the transaction sender. As block space is limited and defined by the protocol, miners are expected to give higher priority to transactions with a larger fee/byte ratio.
2.2.4 Mining pools
In pool mining, miners work together to mine blocks. Pool participants share their computational power to solve proof-of-work puzzles. In case a solution is found, block rewards are split proportionally to each miner’s contributed computational power (Kent and Bain, 2022). At the beginning of the Bitcoin history, the computational power of a personal computer was enough for participating in the mining competition. As Bitcoin’s popularity exploded, the network hash rate skyrocketed, leading to a tremendous increase in proof-of-work difficulty. Nowadays, running an individual mining business is energy and capital intensive. Massive investments in computer hardware (such as GPUs or ASICs) are required. In this scenario, mining pools give small players a way to enter the mining game, when their processing power is so low that individual mining isn’t practical (Kent and Bain, 2022).
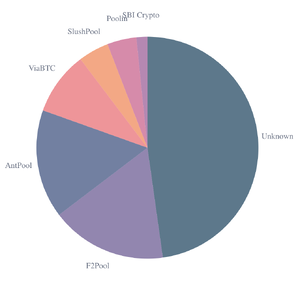
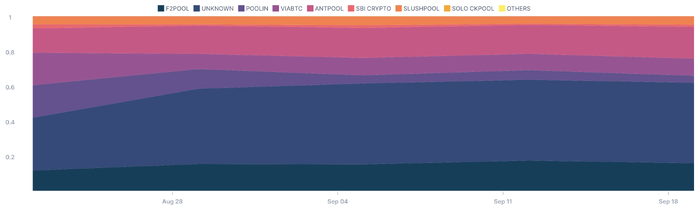
Mining pools increase the level of centralization of the network. For example, out of the 563 Bitcoin blocks mined between September 23-27, 2022: 95 were mined by F2Pool, 89 by AntPool, 52 by ViaBTC, 25 by SlushPool, 24 by Poolin, 9 by SBI Crypto (Blockchain.com, accessed on 2022-09-26). Figure 4 shows an estimation of the hashrate distribution amongst the largest mining pools between September 23-27, 2022 (Blockchain.com, accessed on 2022-09-26). Figure 5 represents how the hash rate distribution has changed between September 27, 2019 - September 27, 2022 (Blockchain.com, accessed on 2022-09-26).
2.2.5 Proof-of-work environmental issues and proof-of-stake
Proof-of-Work crypto mining drains a significant amount of energy and requires massive investments in computer hardware, thus generating carbon-dioxide emissions and electronic waste. An alternative and more environmental-friendly consensus mechanism is proof-of-stake (PoS). Ethereum, which is the most important blockchain together with Bitcoin, trasitioned from proof-of-work to proof-of-stake on September 15, 2022. The adoption of proof-of-stake was expected to reduce Ethereum’s carbon-dioxide emissions by 99.95% (Ethereum website, accessed on 2022-08-17). In proof-of-stake, validating nodes (equivalent to mining nodes in proof-of-work) stake some capital and put it at risk of being eroded or even completely destroyed in case they act dishonestly or lazily (e.g., proposing a block that contains a double spending transaction). In the Ethereum proof-of-stake implementation, users willing to participate as validators are required to commit 32ETH (more than $54 thousand as of 09-09-2022) as a guarantee, or collateral. In proof-of-stake, there is no cryptographic contest, and the validator in charge of proposing a new block is randomly selected. In addition to randomness, the selection process may factor in additional elements, such as the amount and the age of the stake (Kent and Bain, 2022).
2.3 Forks
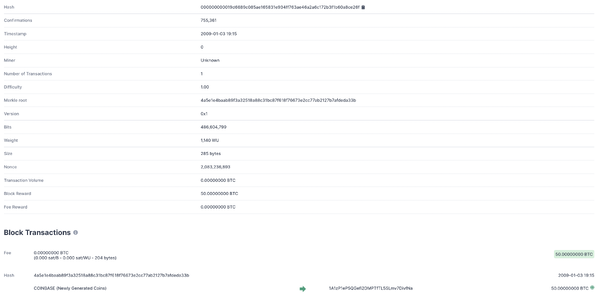
In a blockchain, a block is associated with a specific “height”, i.e. a number in the numbered succession of blocks that constitutes the blockchain. In other words, if a block is the block of the blockchain sequence (with starting from 0), its height will be . The first block ever created is called “genesis block” and has a height of 0. In the Bitcoin blockchain, the genesis block was created back in 2009 by Satoshi Nakamoto, and contains the coinbase transaction by which the first bitcoins where created (at the time 50 new bitcoins were issued per mined block). Figure 6 shows the Bitcoin genesis block as documented by Blockchain.com, accessed on 2022-09-26.
In a physiological setting, each block should be uniquely identified by its height, as only one block at the time should be appended to the blockchain. However, it could happen that two blocks are added on the top of the blockchain at the same height. This scenario is known as “fork”, as the blockchain series splits in two branches. Forks can be accidental or intentional (Wikipedia, accessed on 2022-09-23).
For example, an accidental fork could happen when two miners mine a block nearly at the same time. In this case, only one of the two blocks will “survive”, while the other will be abandoned (“orphaned block”). As consensus rules establish that the longest chain always prevails, the surviving block is the one on the top of which the following blocks will be sequentially appended. All the transactions contained in the orphaned block, and not in the surviving block, are reverted to the “pending” status and returned to the mempool (Antonopoulos, Andreas M., 2018). These transactions will become part of the blockchain history as soon as they will be included in a valid block.
Intentional forks are caused by changes to consensus rules, and can be classified in “soft forks” and “hard forks”.
A soft fork results from a tightening of consensus rules. As the new rules are more restrictive than the old rules, blocks that are created according to the new rules are accepted by all nodes, even by those following the old rules. On the contrary, blocks created according to the old rules may be rejected by nodes following the new rules. Let’s make an example. If the maximum block size is 4MB, and we want to reduce this limit to 1MB, we are making consensus rules more restrictive. A 0.9MB block will be accepted by both nodes enforcing the old and the new rules, but a 1.2MB block will be recognized as valid only by nodes enforcing the old rules. As the adoption of the new rules increases, not-upgraded miners realize that their blocks are getting rejected and are incentivized to upgrade to the new rules.
A hard fork happens when consensus rules are relaxed. As the new rules are less restrictive than the old rules, blocks created according to the new rules may be rejected by nodes enforcing the old rules. For example, if the maximum block size, which was 4MB according to the old rules, is increased to 10MB, a new-rule compliant 5MB block will be rejected as invalid by nodes enforcing the old rules. If there is not unanimous consent about upgrading to the new rules, this causes a permanent split of the original blockchain in two distinct blockchains (Acheson, Noelle, 2022). As a hard fork creates two parallel blockchains, it also results in two separate native cryptocurrencies. For example, Bitcoin Cash is a spin-off crypto deriving from a hard fork of Bitcoin that took place in 2017. Since the two blockchains share the same transaction history up to the fork point, users holding a positive balance of the original crypto, are also entitled an identical balance of the spin-off crypto after a fork takes place (Binance academy, 2022). For example, a user holding 5 original coins before a fork, ends up with 5 original coins and 5 spin-off coins after the fork. As spin-off cryptos are powered by separate blockchains, with specific rules and characteristics, their price diverges from the one of the “parent” crypto. For example, as of September 23, 2022 the prices of Bitcoin and Bitcoin Cash were $18,698 and $113.64 respectively.
2.4 Transactions
In this subsection we explain how bitcoin transactions work through simple examples.
2.4.1 Keys and addresses
Alice wants to enter the Bitcoin world, but she has no idea where to begin. The first thing Alice should do is generating a private key, a public key, and one or more addresses. These alphanumeric strings allow Alice to send and receive bitcoins.
The private key (e.g. 3aba4162c7251c891207...) allows Alice to “unlock” and spend her bitcoin funds. By using the private key, Alice can prove the ownership of her bitcoins. The private key must be kept secret and stored safely. Anyone having access to Alice’s private key can irreversibly spend her funds. Furthermore, Alice cannot spend her bitcoins if she loses her private key.
The public key (e.g. 045c0de3b9c8ab18dd04...) and the associated address(es) (e.g. 1thMirt546nngXqyPEz532S8fLwbozud8) allow other users to transfer funds to Alice. Bob is a friend of Alice and wants to send her some bitcoins. To do so, Bob can transfer bitcoins to Alice’s public key or to one of her addresses. Bitcoin users typically send funds to addresses, and not public keys.
There are several tools for generating a private key, a public key, and an address. Alice decides to use one of these tools named BitAddress. She connects to the web page and gets a pair of keys (public and private) and an address in a few clicks. Furthermore, BitAddress allows Alice to generate additional addresses associated to the same public key (Garavaglia, 2022).
Let’s explain how BitAddress generates Alice’s keys and addresses.
First, BitAddress creates Alice’s private key. The private key is simply a number, picked at random. Alice’s private key, in hexadecimal format[4], is:
3aba4162c7251c891207b747840551a71939b0de081f85c4e44cf7c13e41daa6
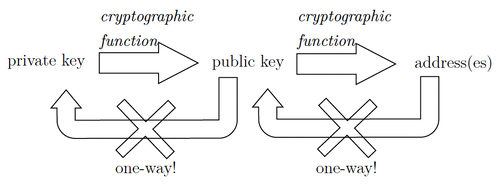
Secoond, BitAddress generates Alice’s public key by applying a one-way cryptographic function to the private key. “One-way” means that given the function y = f(x), it is possible to derive y from x, but not x from y. Thus, sharing the public key with other users is not risky as the cryptographic function cannot be reversed-engineered to obtain the private key. Alice’s public key, in hexadecimal format, is:
045c0de3b9c8ab18dd04e3511243ec2952002dbfadc864b9628910169d9b9b00bcefdd4347074d44bd7356d6a53c495737dd96295e2a9374bf5f02ebfc176
Lastly, BitAddress generates one or more addresses from Alice’s public key by applying a one-way cryptographic function. The address(es) are derived from the public key, but it is not possible to derive the public key from the address(es) (“one-way”). (One of) Alice’s address(es) is:
1thMirt546nngXqyPEz532S8fLwbozud8
Figure 7 summarizes the derivation relationships between the private key, the public key, and the addresses.
2.4.2 Wallets
A wallet is a device, physical medium, program or service that is used to store the pair of keys and the address(es). The simplest example of wallet is a sheet of paper (paper wallet, see Figure 8).
The paper wallet in Figure 8 reports the private key (on the right) and the Bitcoin address (on the left). The information is provided both in string and QR code format. A QR code is a type of bar-code that can be scanned using a smartphone camera. QR codes provide a more agile way to copy the private key and the address from the paper wallet to a mobile device.
There are many types of wallets, beside paper wallets: desktop wallets (installed on a personal computer), mobile wallets (running on a smartphone), web wallets (accessed through a web browser), hardware wallets (specific tech devices). You can try several wallets and choose your favorite one (Antonopoulos, 2017).
Notice that a wallet stores keys and addresses. You cannot store bitcoins in a wallet, as you cannot hold bitcoins in a “physical” sense. Your bitcoin balance, which is associated with your keys, is derived from the blockchain transaction history.
2.4.3 Where to buy bitcoins?
Alice has set up a wallet but she doesn’t know where to buy bitcoins. Several options are available (Antonopoulos, 2017):
- she could buy bitcoins on a crypto exchange and pay in local currency;
- she could ask Bob to sell her bitcoins in exchange for cash;
- she could sell some products or services, and accept payments in bitcoin;
- she could use a bitcoin Automated Teller Machine (ATM), that allows users convert cash in bitcoin.
2.4.4 How to transfer Bitcoins?
Alice wants to transfer bitcoins to her friend, Bob. To do that, Alice:
- opens her mobile wallet;
- imports Bob’s address by scanning a QR code generated by Bob’s mobile wallet;
- selects the amount to be transferred;
- taps on transfer.
As Alice taps on transfer, the wallet structures the transaction and sends it to the network.
Let’s explain the technical structure of a bitcoin transfer. First, we must clarify the concepts of “transaction inputs” and “transaction outputs”. Bitcoin transactions consummate bitcoins owned by the transferor (transaction inputs) and generate bitcoin amounts entitled to the receiver(s) (transaction outputs). When you transfer bitcoin, the transaction inputs must be the outputs of a previous transaction you have received and not spent yet (Unspent Transaction Outputs, UTXOs). As we have explained in 2.4.1 Keys and addresses:
- the private key is needed for “unlocking” and spending your bitcoin funds, i.e. for using UTXOs as inputs in a new transaction;
- the public key and the address(es) are needed for entitling the transferred funds, i.e. the transaction outputs, to the desired recipient(s).
The following example will clarify the relationship between transaction inputs and outputs. Alice (address 1thMir...) transfers Bob (address 1A1zP1...) 0.02 BTC. The corresponding (simplified) blockchain entry will be:
FROM address 1thMir... 0.02 BTC
transaction input
= output of a previous transaction in which Alice acted as receiver
TO address 1A1zP1... 0.02 BTC
transaction output
Bob (address 1A1zP1...) decides to transfer Carla (address 1Hu13C...) the 0.02 BTC he has received from Alice. The corresponding (simplified) blockchain entry will be:
FROM address 1A1zP1... 0.02 BTC
transaction input
= output of “Alice-to-Bob” transaction
TO address 1Hu13C... 0.02 BTC
transaction output
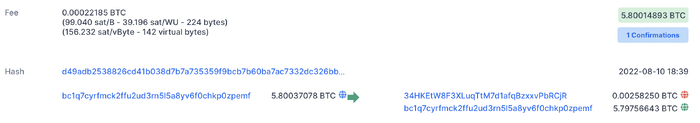
Let’s consider a real transaction such as the one reported in Figure 9.
This transfer uses a single input, which is reported on the left-hand side of the arrow. It is a UTXO of 5.80037078 BTC. You can read the transferor’s address (bc1qtc...) next to the input amount.
The outputs are recorded on the right-hand side of the arrow:
- a payment of 0.00258250 BTC is sent to address
24HKEt...
- a “residual” of 5.79756643 BTC is sent back to the transferor’s address (
bc1qtc...)
The total input amount is slightly higher than the total output amount; the difference is a fee paid to the miner that will include the transaction in the blockchain. See subsection 2.2 Consensus mechanism for further details.
total inputs = 5.80037078 BTC
total outputs = 0.00258250 BTC + 5.79756643 BTC = 5.80014893 BTC
fee = 5.80037078 BTC - 5.80014893 BTC = 0.00022185 BTC
Figure 10 provides a further example of a bitcoin transaction. Let’s assume that Alice received bitcoins separately from Lily, Tom and Joe (0.001 BTC, 0.001 BTC, 0.002 BTC). Now, she wants to send Bob 0.003 BTC. With her private key, Alice unlocks the unspent outputs of the three previous transactions. These UTXOs become the inputs of the new transaction addressed to Bob, which in turn generates two new outputs (0.003 BTC to Bob, 0.0009 BTC back to Alice as a “residual”). The fee to the miner is 0.0001 BTC.
- ↑ You interact with this architecture every times you visit a web page. To visit a web page you must install a web browser, e.g. Google Chrome, on your PC. Google Chrome is a client software. When you visit a website, e.g. www.wikipedia.org, Google Chrome sends a requests to a web server that returns the desired web page.
- ↑ To run a node you must install appropriate software.
- ↑ The concept of proof-of-work was first introduced in the ’90s to deter abuses on a network, such as spam. Sending an e-mail is not costly, and therefore spammers can freely send thousands, or even millions, of e-mails to their victims. To avoid this, you can require senders to do some computational work (e.g. solving a mathematical puzzle) before being able to send an e-mail. In this way, you overwhelm spammers with a significant computational burden, thus hampering their activity (Dwork and Naor, 1992).
- ↑ The hexadecimal number system is a number system in base 16, i.e. it uses 16 symbols instead of the 10 adopted by the decimal number system. These symbols are
0,1,2,3,4,5,6,7,8,9,a,b,c,d,e,f. The private key reported in the example in decimal format is: 26563230048437957592232553826663696440606756685920117476832299673293013768870.